
6 smart goals of revenue cycle management…
Goal setting is a game changer. Every healthcare organization has RCM milestones they want to hit or metrics they’d like to…

5 strategies to reduce future cybersecurity threats…
If you’re a leader in healthcare revenue cycle management, cybersecurity threats are a top concern — and they have to…

5 strategies to overcome patient payment complexities
Healthcare organizations need to simplify patient payment collection — that’s how your patients see it anyway. Whether they’re buying a…

5 most unproductive touches in the healthcare…
Note: This post was originally published in May 2023. It was updated in January 2024. The healthcare RCM process…

Revenue cycle 101: What is denial management…
Denial management in healthcare RCM is critical. Denials affect everything from revenue flow to efficiency to patient satisfaction. And when…

Waystar Advisory Board: 5 takeaways from our…
To kick off our first annual True North conference, the Waystar Advisory Board met in September 2023 at The Grand…

Rev cycle 101 - Healthcare revenue cycle…
In the healthcare revenue cycle, acronyms are common — and also critical. Whether you’re in charge of denial prevention or…

Revenue cycle 101: Referral status, authorizations vs.…
If you’ve ever had to chase down referral status from a payer, you know it’s a tedious, time-consuming process. Whether…

Revenue cycle 101: Prior authorization + referrals
[Note: This post was originally published in January 2021 but was updated in October 2023] Prior authorization. Pre-authorization. Precertification. Prior…

3 achievable strategies from Piedmont for healthcare…
Ensuring patients can understand their healthcare statements — and receiving payment in a timely manner — go hand-in-hand. When statements…

Research on denial management in healthcare: 3…
Did you know unresolved claim denials can represent an average loss of up to 5% of net patient revenue for…

Healthcare denial management debrief: 4 top reasons…
Today, healthcare denial management is not just a priority for RCM professionals — it is the priority. "In recent surveys, three…
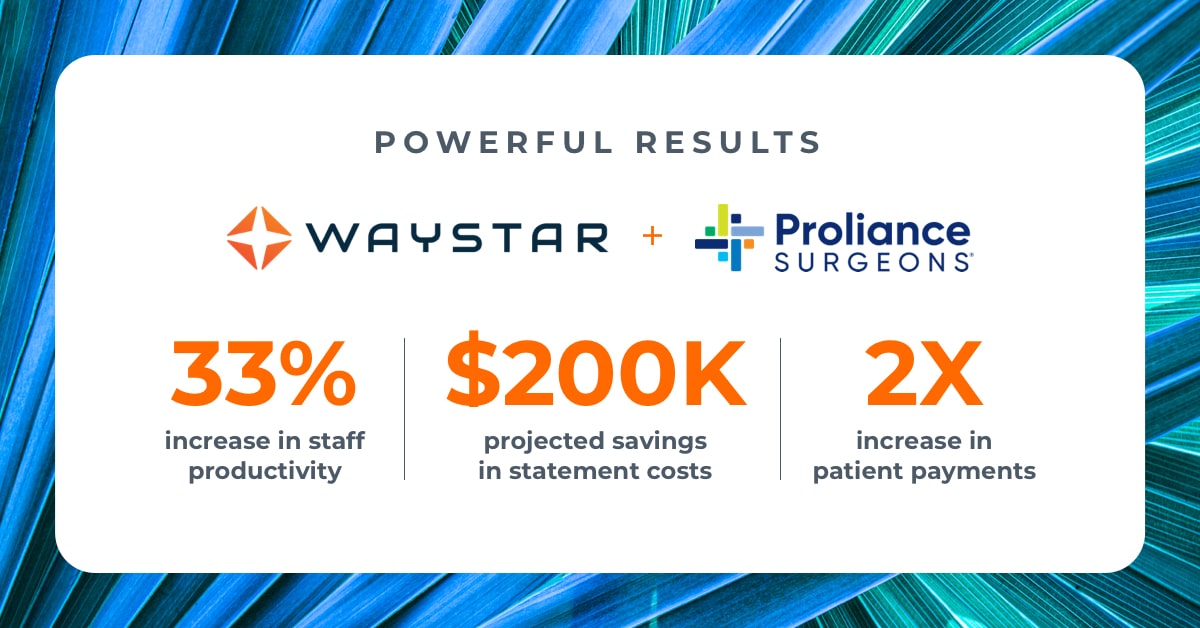
Steps for revenue cycle optimization success: 3…
As health organizations expand and scale their business, having cutting-edge solutions is critical to streamline their revenue cycle. That’s exactly…

Delivering better patient financial care: 3 takeaways…
When it comes to earning patient loyalty, many focus on the clinical side of healthcare and may not realize just…

5 revenue cycle management strategies to boost…
Revenue cycle management strategies are a dime a dozen. So, how do you know which ones will actually boost productivity?…

Develop a data-rich dashboard: Which medical billing…
This is the eighth and final post in a new Waystar blog series: 7 steps to sharpen your healthcare…

THMA report: 3 facts about today's patient…
Today, the patient financial journey has the power to define a patient's entire healthcare experience. It sounds hyperbolic, but the…

Boost post-service patient collections in healthcare (in…
This is the seventh post in a new Waystar blog series: 7 steps to sharpen your healthcare revenue cycle.…

Get your organization out of denials in…
This is the sixth post in a new Waystar blog series: 7 steps to sharpen your healthcare revenue cycle.…

Opting into intelligent automation in healthcare? Start…
This is the fifth post in a new Waystar blog series: 7 steps to sharpen your healthcare revenue cycle.…

4 top tips to revamp your point-of-service…
This is the fourth post in a new Waystar blog series: 7 steps to sharpen your healthcare revenue cycle.…

